New Cybercrime Scam Impersonates HR: How to Protect Yourself
What Happened?
A cybercrime group called Storm-2657 has been targeting university employees to steal their paychecks. These attacks started in March 2025 and have affected at least three universities, with phishing emails sent to over 6,000 people across 25 institutions. The attackers are not hacking the payroll systems directly — they're tricking people into giving up access to their accounts.
How the Scam Works:
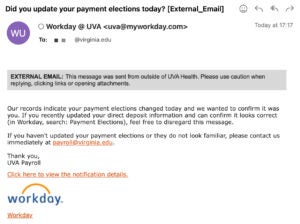
1. Phishing Emails: Attackers send fake emails that look like they’re official Human Resources notifications (e.g., from HR, organizational leadership, or health alerts).
2. Fake Login Pages: These emails link to fake websites that look like real login pages (e.g., Workday).
3. Credential Theft: When users enter their login info and MFA (multi-factor authentication) codes, the attackers steal their credentials.
4. Account Takeover: Using the stolen info, attackers log into the victim’s account.
5. Redirect Paychecks: They change the direct deposit settings so the victim’s salary goes to the attacker’s bank account.
6. Covering Their Tracks: They set up email rules to hide alerts from HR systems, so victims don’t notice the changes.
How You Can Protect Yourself
Here are some simple but powerful steps you can take to protect yourself (and UVA Health!) from this scam:
1. Only Approve Duo MFA Push Notifications That You Requested
- If you receive a Duo MFA app push message that you didn’t request, be sure to deny the fraudulent authorization — we are so accustomed to selecting “Approve” when we receive Duo push messages that we can inadvertently tap approve when it wasn’t a request that we put in.
2. Never Click Suspicious Links
- If you receive a suspicious email about payroll or benefits alerts:
- Don’t click the link or download any attachments.
- Instead, go directly to the official UVA Health Workday portal or contact UVA Health HR to verify the legitimacy of the message.
3. Watch for Emails with Urgent or Emotional Language
- Phishing emails often try to scare or rush you into making a decision to click a link or download an attachment (e.g., “You’ve been exposed to illness!” or “Your benefits are changing!”).
- Stop and take a moment to think before you click.
4. Check Your Inbox Rules
- Attackers may set up rules to hide warning emails.
- Go to your email settings and look for inbox rules you didn’t create.
5. Review Your Duo MFA Settings
- Make sure your phone number or device is the only one listed for MFA.
- Remove any unfamiliar devices or numbers.
6. Report Suspicious Emails
- If you receive a suspicious message, report it using the UVA Health “Report Suspicious Email” button in Outlook.
If you have any questions or concerns regarding an email that you have received, please do not hesitate to reach out to HIT Security by submitting a ServiceNow ticket.
Final Thoughts
These attacks don’t exploit flaws in systems like Workday — they exploit human trust and weak security setups. UVA Health has implemented technical controls to reduce the chances of this type of attack going through, however we all need to strive to avoid clicking on suspicious content. By staying alert and following the steps above, you can help protect yourself and UVA Health from becoming a victim.
Latest News